Ponemah Data Security Export/Import Security Settings
Overview
The Data Security Settings Export/Import Utility allows a user to quickly copy all Data Security settings (User List, Access Levels, and Security Preferences) defined from one workstation to another. Previously, all Data Security settings would have needed to be configured on each workstation, individually.
This utility is included with Ponemah versions 5.20 Service Pack 8 (SP8) and later, however accessing the program has changed:
Ponemah version 5.2 SP8 - The utility is accessible from the C:\Ponemah\SecurityApplication folder.
To run the utility, double left-click on Ponemah.SecurityApplication.exe and the Ponemah Security Utility dialog will be displayed. This utility may only be run by a Windows Administrator. If a Windows Administrator is not logged in, attempting to run the utility will result in being prompted for Administrator login credentials.
NOTE: You may run this utility on a workstation that does not have SP8 installed. To do this, the Utility may be run from any location, such as a USB flash drive or network drive, as long as the files located within the Security Application folder are copied to that location.
Ponemah versions 5.30 and later - The utility is accessed through the P3 Admin program. The Ponemah Admin application is found under Start – All Programs – Ponemah Admin.
Using the Utility - Exporting Security Settings
To export the security settings from a previously configured workstation:
- Double left-click on SecurityApplication.exe to display dialog, as shown below.
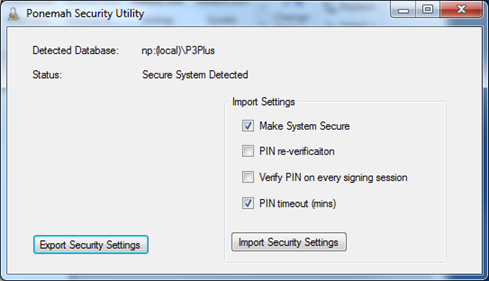
- Click on the Export Security Settings to save the current security information.
Note: the system must be secured to enable the Export Security Settings - Enter a file name and location for the file to be saved.
- Click Save to create an Excel output file.
- Transfer this Excel file to any subsequent workstation intended on having the same security settings.
Importing Security Settings
The Data Security Option should be installed and functioning on the system prior to importing security settings.
WARNING: Upon importing security settings, ALL settings currently configured on the system will be deleted and replaced with the imported settings. This includes all users, access levels and other features specified during the import.
To import the security settings from a subsequent workstation:
- Launch the Ponemah Security Utility from the intended workstation.
- (Optional) The Import Settings menu permits additional functionality to be copied over from the original workstation that generated the export file. If checked, the function will be enabled on import and the current settings from the export file will be utilized. Each setting is described below.
- Make System Secure (Only for Ponemah 5.2): If the workstation receiving the imported security settings is not currently secured, checking this checkbox will automatically secure the system.
Note: Checking this box does NOT secure any existing directories, nor does it create any new secured directories. - PIN/password re-verification (depending on Ponemah version): This will enable the PIN (Ponemah 5.2) OR Password (Ponemah 5.3 and later) reverification feature which will prompt the user to re-enter their PIN/password after the designated time in minutes. This will only enable the feature but will not change the current time (in minutes) that is specified within the dialog.
- Verify PIN/password on every signing session: This will enable the feature to verify the PIN/password upon every signing session.
- PIN/password Timeout (mins): This will copy the current time in minutes from the original workstation which generated the security settings Excel export file and update the time for PIN/password re-verification when imported into the new workstation.
- Make System Secure (Only for Ponemah 5.2): If the workstation receiving the imported security settings is not currently secured, checking this checkbox will automatically secure the system.
- Click the Import Security Settings
- Browse to the location of the Excel file that was exported from the original workstation.
- Select the file and click Open to import the settings.
- The Get Reason dialog will appear allowing a reason for change to be entered. The text entered here will be placed into the Application Log for traceability.
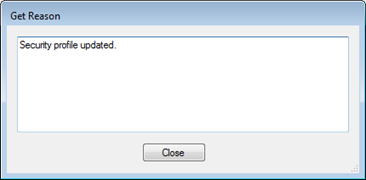
- Click Close to save the entered reason.
- Click OK.
Verifying Security Settings Import
Once imported, verify changes by logging into the Ponemah Admin application. View the Setup Access Levels, Setup User List and System Security Preferences menus to verify the changes were made.
All changes and the reason entered for the changes are logged in the Application Log and will be stored with the system. This log may be exported from this dialog for your records.

Comments
0 comments
Please sign in to leave a comment.